Business and IT are now changing with a rapidity never before seen while at the same time budgets are under close scrutiny. Many aspects of IT investment are expected to show demonstrable returns to the business before any project can be sanctioned. The rapid evolution of IT means that securing IT systems and services is challenging in its own right. However, the threat landscape is changing in a rapid, dramatic, and often under-recognised fashion.
When assessing the threat readiness of an organisation it is essential to have to hand some fundamental information. This information clearly needs to take account of the business operations of the organisation, its existing IT infrastructure along with the type and context of usage made of IT systems by users. It is important to remember that no matter how accurate this data is – and for many it can far from complete or up to date – the most important requirement is to consider business operational processes in the context of existing security threats. As both the IT infrastructure, the way users employ IT systems and the threat landscape are anything but stable it is essential that this review process be performed periodically rather than as a one off event.
Looking closely at the security threats to which organisations are now exposed there are several areas to address. First amongst these is a direct appraisal of existing technological threats, the area most closely associated with IT security, e.g. Worms, virus infection, “drive by” infection from Web page browsing. In addition it is necessary to look at how people use IT systems and the processes associated with routine business operations. For example, do users know how to protect sensitive information, or even which data is sensitive, do they know what to do if they receive a suspicious mail that may by phishing for information?
Whilst the natures of external IT threats become more sophisticated day by day, it should never be forgotten that the weakest link in many security processes are the users themselves and the way they use, accidentally misuse or even abuse IT systems. Many security breaches occur when people do something that they should not or, just as likely, do not do something they should.
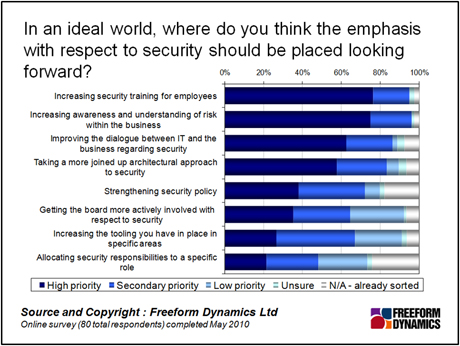
For this reason it is interesting to note that the survey results above show that many organisations now recognise that the people factor needs to be addressed as a top priority, at least in an ideal world.
When looking at the technology side of things, the figure below shows how well protected organisations considered themselves to be just over a year or so ago, and also highlights just why it is that the people problem is rated so highly as a priority.
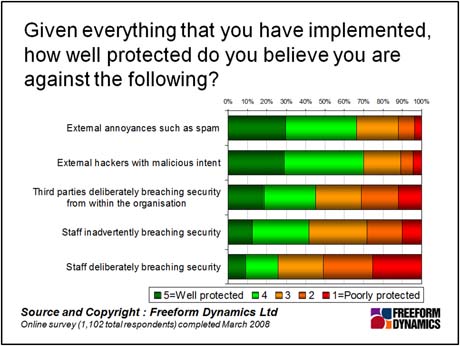
The figure is revealing in many ways. First off it highlights that whilst many “obvious” threats are considered by the majority to be well under control, a sizeable community acknowledges that even the annoyance that is spam could be better managed. But the rest of the chart should cause some concern, especially given that the nature of external threats are moving forward rapidly with attention now firmly focussed on commercial exploitation.
Whilst the technical evolution of modern malware has been rapid making the protection of systems ever more complex it is important to recognise that the motives of those creating the new threats has also changed dramatically in the last few years. No longer are malware authors releasing their creations just to garner notoriety or to inconvenience people.
Today malware is more usually created with financial or political goals in mind. In many respects the threat creation community has become a business vertical with malicious code authors, or sometimes groups working together, attempt to get hold of “data” that can then be transformed into monetary rewards. Indeed, the threat creation community is better described today as the malware commercial exploitation industry, and as such these groups are targeted with clear commercial goals and are often better funded than regulators, crime fighting agencies and the security groups of the majority of businesses.
Password stealers, credit card and account number / pin seekers are now routine targets of malware infection with the authors of the infection either using the information themselves or selling it on for others to exploit. “Identity theft” should now be a major consideration for all IT systems users, at work and at home. It is now also commonly assumed that some nation states and other politically active groups are fully engaged in what has become known as “Cyber attacks”.
The threat creation industry has also ramped up the speed at which it operates, mimicking, and in many ways surpassing, the fast developments of both business operations themselves and the security industry seeking to protect their IT systems and users. This factor must be coupled with the reality that the vast majority of attacks now work in “stealth mode”, actively taking steps to remain unnoticed on compromised systems. This combination makes life much harder for IT managers and security specialists to work out just how vulnerable they are or whether any systems have been compromised.
Along with the changing nature of the IT threats and their modus operandi, organisations need to take into account that the vectors of initial infection have also spread to include many more routes than the simple floppy disk and e-mail attachment of days gone by. Today so called “drive by” infections are becoming increasingly common as the first source of infection of computers. This infection method is initiated when a user accesses a compromised Web site, often sites of respectable entities. Vulnerabilities in the Web browser itself or tightly coupled programs and plug-ins, are used to insert malicious code, key loggers or Trojans onto the users machine. Another vector, namely infection via the use of compromised USB sticks, has taken off in parts of the Asia-Pacific region and is spreading around the globe.
Security and IT managers also need to take note that only a half of organisations consider themselves to be well protected against third parties based inside the firewall breaching security. Of more concern, fewer than a third thinks they are well protected against their own staff deliberately breaching security. Taken together these results support the often unvoiced concern that the serious security challenges are to be found inside the enterprise itself rather than solely on the outside.
With changes such as these to the overall threat landscape and the ease with which anyone can now create malicious code using “toolkits” freely available on the web, it is clear that securing the enterprise, and the home user, are factors of higher importance than ever before. The current dark economic climate coupled with an ever-increasing proportion of the world’s population getting online will further exacerbate the threats, as will the commercial exploitation of successful attacks by the selling on of tools and experience.
The rise of home working and managers looking to access corporate IT systems from wherever they may be is making securing the enterprise more complex. In order to deliver effective, secure IT services it is necessary to understand what IT assets are deployed in the company, for what they are being used and by whom. In most organisations the quality of this knowledge is usually neither sufficient nor up to date. Without having ready access to this information it is nigh on impossible to evaluate the nature of potential threats in the context of business risks and to protect systems, and users, appropriately. IT security threats have become an industry and organisations must recognise this in order to invest in effective solutions and to train their users how to work securely.