Security has long been the poor cousin of IT. As any security professional knows, the way we have traditionally implemented security is tantamount to a technological afterthought. Through the years we have attempted to block holes, protect the periphery and lock down access rights for running systems, in the knowledge that IT security is all too often too little, too late.
We could of course blame budgeting mechanisms, in that there never seems to be enough money to go around, and IT security often seems to be the first thing to go when speccing out new systems. It’s common knowledge in the industry, for example, that ‘fear’ still drives much of IT spending. You can’t beat a good press headline about data leaks, malicious websites and so on to trigger a release of funding for whatever product is in vogue at the time.
For similar reasons, IT security has traditionally been a domain for such security specialists. From its roots in encryption and obfuscation, the discipline has attracted a certain breed of person – from mainstream experts in risk and protection, through to those folks who go under pseudonyms and hang out in obscure chat rooms. It’s a good job that such experts have been in place, given that the technical majority have not really seen security as their thing. But is this set to change?
In a recent poll we were looking at how organisational trends might have an impact on IT security practice. Out of a broad set of potential areas, the need to secure mobile technologies rose to the top of the list, together with the requirement to reduce the risks of remote access from the field (Figure 1).
As you can see and in line with tradition, this is still as much (if not more) about securing the technologies involved, as ensuring that working practices are appropriate. The implication however, is that security is only going to become more fragmented and complex compared to the days when the majority of us were office-bound.
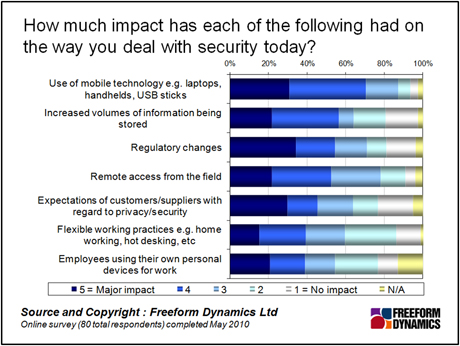
Figure 1
Incidentally, while regulatory changes may only be in third position right now, we get the impression from poll respondents that it’s looming on the horizon (Figure 2). Perhaps this is the perception that sooner or later the bureaucrats will catch up with us, or perhaps there really are regulations that will come into force. We shall have to see.
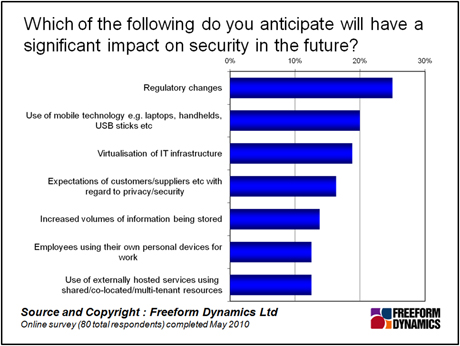
Figure 2
The big story here, however, is how the balance is changing in terms of who should be involved in the security decision making process. As you can see from Figure 3, security specialists and those in specific management roles have traditionally dominated security decision making. However the mix of roles involved in security decisions looks set to change significantly.
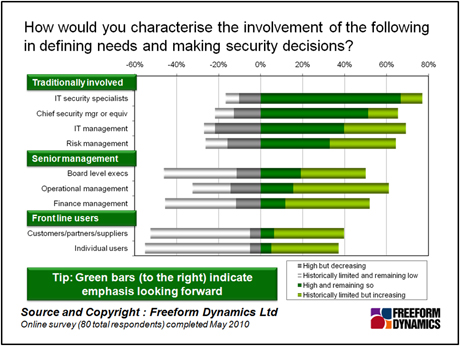
Figure 3
The roles shown in the figure above can be considered in three categories. First off we have those individuals who have arguably been involved in security decisions for a while – security specialists, security managers and IT managers, as well as risk managers who (while a more recent phenomenon) are more prevalent in certain sectors.
The second group is that of senior management – board level executives, operational and finance managers. What’s very interesting here is that, while the involvement of the roles in this group has traditionally been quite low, it is certainly ramping up, according to respondents. This is evidence indeed that business management is taking more interest in the role of security, as it moves from being more about the technology, towards areas such as business risk.
Finally in this chart, we have the front line recipients of IT – from customers and partners, to individual business users. From a minimal start, these individuals are also seen as having a far greater say in how IT security is done. This isn’t the case for everyone, as illustrated by those who responded: “Historically limited and remaining low.” Why should this be?
The most straightforward conclusion to draw is that IT security is evolving into more of a business-level discussion. We know this is a good thing, for the simple reason that ‘the business’ is in a far better position to decide the risks, than anyone in IT. This isn’t to belittle the specialists: as poll respondents have highlighted, the role of the security expert is not going anywhere. However, IT is not always the best vantage point to second guess what’s going on in the heads of business managers.
A simple example of this is captured in the question from the finance director I used to work for as an IT manager, when I proposed a security mechanism of any form. “Do we really need it?” he would ask, leaving me the difficult task of trying to explain why it was important. Now, had the FD been on top of what risks his business faced, it would have been him coming to me with a requirement, which is a much better starting point particularly when funding is involved.
For more clarity on this drive towards greater business involvement, we can look at another set of responses from the poll, notably where the emphasis should be placed in terms of security priorities (Figure 4). Staff training and awareness raising come out as joint top, followed by improved dialogue between IT and the business – a triple whammy for ensuring that everyone in the business knows what needs to be secured, why and how. Indeed, improving technology alone came way down the list.
Right at the bottom of the list is allocating security to a specific role, which drives home the point about needing to see the security role as one piece of the puzzle.
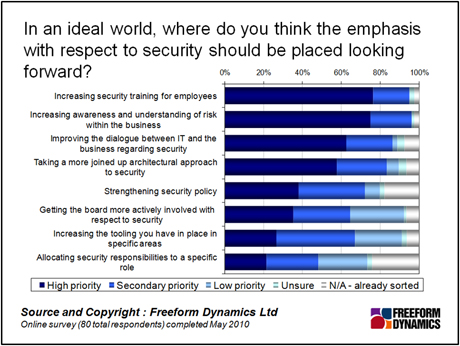
Figure 4
So, does this mean that we will see the demise of the security manager? Anyone who has worked in such a complex field as security will know that the importance of the specialist roles, either in management or in an advisory capacity, is not going to diminish any time soon. What the evidence does suggest however is that the role itself may evolve into more of a facilitating capacity, rather than the traditional voice in the wilderness position that has traditionally dogged IT security in general, and the people responsible for it in particular.
If you’re a security manager or similar, we would of course be interested in hearing from you.
Content Contributors: Jon Collins