We tried to get through this workshop without using the five letter C-word, but we could not quite make it to the end. There are good reasons for considering whether cloud will have an impact on security – not least because it is being discussed so much that you need to know if there is any substance behind the hype.
What’s the hype? We need to recognise that the term “cloud” is used to refer to a multitude of things. It may mean hosted services using shared, co-located or multi-tenant resources – an evolution of hosting.
Also vendors are using the word when speaking about using internal IT resources in highly virtualised, dynamic pools. This is an internal, private cloud. This is a similar path to the adoption of other IT service delivery models such as managed services and outsourced IT.
Our main finding is that you don’t need to panic. Over the past few weeks we’ve been researching just how fast this wave is due to wash ashore, and – to put it bluntly – we’re not talking about a tsunami here. Mass adoption of the hosted service cloud model is a long way off, and while the internal, dynamic IT model may come sooner (thank virtualisation for that), there is no need to worry: but there will be problems to solve.
We can see the potential security impact of both with a quick glance at your feedback from a couple of weeks ago.
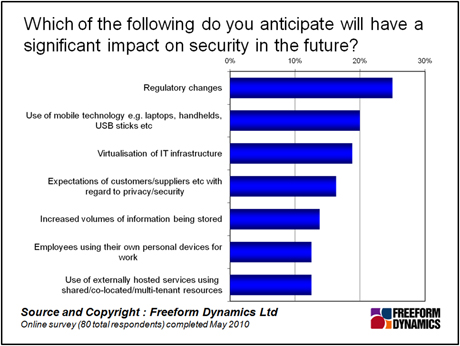
As we can see, along with the usual suspects of regulatory changes and the use of mobile devices, virtualisation of the IT infrastructure is expected to become a factor. Nearly 20% of respondents expected virtualisation to have a security impact, and more than 10% of readers report that the use of externally hosted services will also affect their approach to security. This means that several of the many definitions of cloud computing will be influencing security.
The first challenge is the data itself, be it internal to the business or external to the corporate firewall. Whatever the threats, any measures taken to counter them will need to ensure that data is only available to applications or users as defined by the organisation’s access policy. We’ve covered some of the more elementary challenges around data protection and governance in external cloud systems in a previous workshop. We looked at virtualisation and security a week or two ago too.
Most fundamentally, only those whose role requires them to have access to the data should be able to see it and manipulate it. This leads us to a broader problem. There’s a simple principle involved – namely, that the further away your data is from your centre of control, the more at risk it will be.
Picture this: Even in static IT environments, information security can be problematic; in virtualised, internal cloud systems that can be provisioned rapidly, the challenge is bigger. If your IT facilities are not running on your own hardware, managed by your own administrators, the challenge is increased. If you are utilising many cloud providers for different IT services, the difficulty is exponentially greater.
To complicate matters further, the old IT considerations of multi-vendor interoperability, support and integration also apply. The harder things are to manage, the harder they are to secure.
One approach to tackling cloud security could be to encrypt all data and store the access keys in another location. Of course, managing and securing the keys then becomes the most important problem to solve. But this can help solve many data privacy problems – and possibly even some geographical limitations covering where data can and cannot go. It might be the only long-term solution that avoids over-complicating operational oversight, but encryption can cause as many problems as it solves.
Security is only one element of risk management and governance, and it’s worth considering it within the broader context. For example, if you are using external cloud resources, look at how the data and any intellectual property invested in the processing engines employed to manipulate data can be moved to other third party cloud providers, or back into the enterprise, if you need to do that. You could call this “Cloud Escrow”.
How do you cope with security in hosted systems, or using dynamic approaches to IT? Let us know about the problems you found, and how you solved them.