By Tony Lock
The data held in every business is valuable and in the current economic climate every organisation is looking to exploit as much as possible the information it holds. Whilst the precise nature and value can be difficult to determine precisely, many organisations say the data they hold is amongst their most valuable assets. At the same time many also report it is difficult for them to extract full value from the data they hold. As a consequence, in addition to various legal requirements, nearly every organisation takes steps to protect its business data, though often with variable success.
Two recent papers by Freeform Dynamics – The Data Protection Imperative and Data Protection as a Business Enabler – ask whether there should be more to ‘data protection’ than ‘backup and recovery’ and whether improving information management can help to extract that extra value from corporate information whilst simultaneously improving data protection.
Organisations today are creating ever expanding volumes of information. Indeed, in many areas, the rate at which they add new data to central systems as well as on the growing range of non-central computing devices employed by users is not slowing but accelerating. The protection of data held in central repositories is a well-established science and the choices for protection are many and varied. That said, the task of making such data available to users simply when required is often labour intensive, even supposing the user knows the information exists or has value.
When you start to think about protecting data held on PCs, laptops plus the recent addition of tablets and smartphones, much is more complex and the solutions in some areas are, understandably, less well developed. The fact that many of these are extremely capable computing devices means that users are employing them in an expanding raft of business processes. This, in turn, ensures that the range of corporate information now routinely held on such devices is growing even though many of the devices in use receive little, if any, formal data protection. This challenge is made more difficult by the fact that many of the devices, especially those used by senior managers, may not even be owned by the organisation.
As a consequence the information on these mobile devices, or indeed on home PCs, may potentially put an organisation at risk. The threats involved range from other business users being unable easily to exploit the data created through to corporate scandal or legal breaches should it be lost or corrupted.
Another concern is that should data be lost, it is likely the user will try to insist IT helps in its recovery, even if this is impossible to achieve (because the data was never backed up). This is especially important when we remember that many users today of personally owned tablets in business are senior managers or other ‘influential’ staff with whom it can be impossible, or at least severely career limiting, to say “sorry, it’s your own fault”. IT fears being seen as unable or unwilling to help users in times when business leaders do question the effectiveness of internal IT to drive businesses forwards rapidly.
The fact that so many senior managers end up with ‘unprotected data’ may simply be down to them never asking what they should do or that they found the data protection process to be too intrusive. Or maybe they simply forgot what to do.
While the perils of poor data protection are clear, and many users already have personal understanding of the impacts when things go wrong, the same is not true for the benefit side of the equation. This is especially true when considering how much time is wasted by users trying to get hold of accurate, up to date, information on which to base key business decisions. Some of the impacts achievable through more effective information management and data protection, many of which may have received little attention heretofore, are summarised in Figure 1.
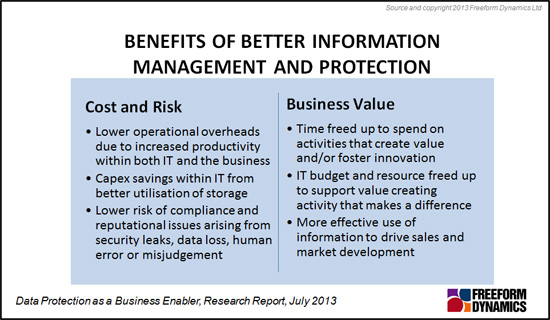
Figure 1
While there are benefits to be had, many organisations seem unable even to start to investigate implementing better data protection or information management systems. This often stems from the difficulties associated with building a convincing business case. Whilst some elements of a project may be relatively straightforward to justify, especially if ‘storage consolidation’ is being considered, others require estimates of the likely ‘business value’. If the latter occur it is essential to ensure that influential stakeholders obtain a good understanding of how they can exploit corporate information more easily.
There are several fundamental steps which organisations can take to improve data protection and information management. Several of these are outlined in Figure 2. They may look simple but they do require effort and commitment, even before any technology enhancements are considered.
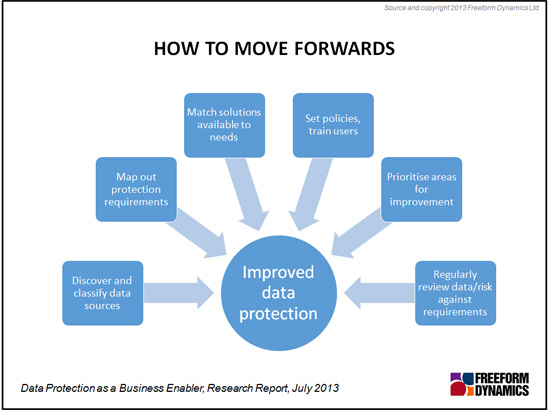
Figure 2
The first of these is to discover all the sources of data in the organisation which hold valuable information. This sounds straightforward but often is not, even though there are software tools to assist which are sophisticated and ‘usable’. Yet few enterprises in Freeform Dynamics’ experience are confident they possess an accurate picture.
The next step is to attempt to classify the data sources, at least to some degree. This is what will enable protection policies to be established for each category. That said, organisations that have been successful in enhancing their data protection and information management capabilities stress that this task should not be tackled all at once, but be broken down into manageable segments, perhaps picking one or two critical date sets first. From then on it is a matter of identifying the protection and information access requirements, and making sure that these are met either via modifications in existing tools and processes or via the introduction of new tools.
Many solutions that were previously considered to be too expensive or complex for widespread deployment — such as Active Archiving, Content Repositories and sophisticated data replication systems to name but three — are now becoming easier to implement, sometimes in the form of ‘cloud services’.
The potential benefits achievable, as well as the opportunity to minimise data protection risks, makes information management and data protection an area which perhaps should be higher up on the list of things to do. With organisations under growing pressure to improve returns while minimising legal and reputational risk exposure, now is a good time to act. The overlap between information management and data protection that some new solutions offer can help improve business case arguments. Indeed, properly scoped it can be possible to get the backing of constituents who might previously have regarded these areas as matters for IT, rather than business enabling capabilities that they can now become.
CLICK HERE TO VIEW ORIGINAL PUBLISHED ON
