Just as IT professionals and others responsible for mobile security have come to terms with BYOD, the problem has moved on, with the lines between business and personal activity blurring even further. Against this background, effective management of mobile risk will increasingly require a user-centric approach.
Soothsayers mistaken?
Those who predicted that BYOD would take over the whole world of mobile working appear to have got it wrong. A recent research study (251 respondents) confirms that company devices still predominate in the business environment by a convincing margin (Figure 1).
Figure 1
The research also suggests that this picture won’t change in a hurry. While the use of personal equipment is on the up, it is misleading to focus on this alone (as some commentators do). Our respondents tell us that deployment of company devices is growing at approximately the same rate, and this is obviously off a larger base.
BYOD in perspective
The truth is that mobile technology use in business is rising across the board. As part of this, BYOD has found its place among certain types of user, often in relation to non-essential secondary devices. However, the emerging consensus is that core business needs are generally best met through equipment procured, deployed and ultimately controlled by the company. This realisation is now acknowledged by many of those caught up in the original BYOD frenzy, hence the recent reduction in levels of industry noise on the topic.
If you are involved in managing or supporting mobile activity this may seem like welcome news. Not quite as good as BYOD dying out altogether, but still better than the total anarchy some have feared. But don’t relax too soon.
The emerging new reality
With all of the attention paid to BYOD, which is essentially about accessing business applications and services from a personal device, it’s easy to overlook a parallel trend that goes the other way – the use of company equipment for personal purposes. As a simple example, over 60% of those taking part in the research said company devices were being used by a significant number of their employees to access personal email.
Put this together with employees using their company smartphone or tablet to access other personal messaging accounts, social media, and even entertainment content, and it’s clear that the concept of a pure business device is increasingly being challenged.
Bring BYOD back into the equation, add in the use of user-selected software and services (BYO apps), and the picture we end up with is one of extensive crossover between business and personal assets and activity (Figure 2).
Click on chart to enlarge
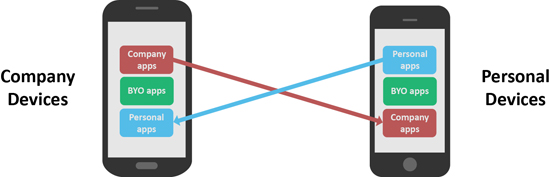
Figure 2 – Extensive crossover between business and personal assets and activity
Against this background, who owns the device is probably the least of your worries from a cost and risk perspective.
The weakest link becomes weaker
Users are generally not brilliant at the best of times when it comes to protecting themselves and the business from IT-related risk. This comes through strongly in the research in relation to mobile security in particular, with respondents highlighting lack of user knowledge and awareness, along with general thoughtlessness, as the most common causes of exposure or uncertainty (Figure 3).
Click on chart to enlarge
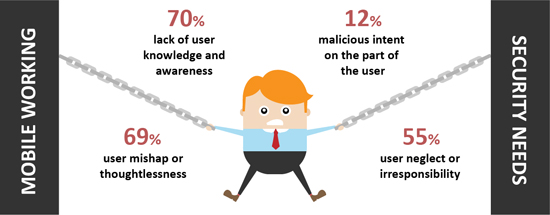
Figure 3 – Employee-related sources of mobile security exposure or uncertainty
The challenge here is aggravated when employees mix business and personal activity in the same environment. Personal apps are often used with an open, sharing mind-set, whereas anything that touches business data requires much more in the way of discipline and control. The risk of misunderstandings, misjudgements and accidents is higher than ever when the user’s two worlds become intertwined.
As a result, the weakest link in the security chain arguably becomes even weaker unless you take appropriate measures.
Taking a hard line approach
One way of dealing with the challenges and risks is to go into lockdown mode. This could be done through strict policies that outlaw the mixing of business and personal activity, backed up by technology measures that restrict certain types of user behaviour. There’s no shortage of options here, from basic mobile device management (MDM), through encryption, content filtering and access control technology, to full-blown enterprise mobile management (EMM) solutions.
Respondents in the research, however, alluded to cost and complexity problems with the lockdown approach. Pushback from users, and even security measure avoidance tactics (employees working around your attempts to constrain them), can then come back to bite if you get too heavy-handed.
Directly addressing the human factor
The best results seem to be achieved by those who blend technology protection with investment in user awareness and training programs. In fact, given the choice between throwing lockdown technology at the problem, or focusing on user understanding and awareness, the evidence suggests that you should do the latter. This makes sense when you consider that no set of protection technologies can ever be totally ‘fool proof’.
The bottom line
It can sometimes seem as if mobile technology has taken over the world of business. The reality, however, is that the majority of organisations are still only scratching the surface of the potential, and most IT departments are still figuring out how best to deal with the trends and developments we have mentioned.
While it’s impossible to predict how activity will pan out in many areas, one thing for sure is that personal and business activity will become increasingly harder to keep apart, even with lock-down and control technologies in place. With this in mind, safe and efficient mobile working depends on addressing the human factor directly by finding ways to close the user knowledge and awareness gap.
It might go against the grain for some, but effective mobile risk management means working with and enabling users as part of the solution, rather than treating them purely as the problem.
If you are interested in reading more please download the study report entitled ‘User-Centric Mobile Security’. You can get your copy here.
