Our recent research highlights that many organisations are considering refreshing their desktop estates or have already begun projects in this area. While it is clear the usual desktop refresh cycle has been interrupted by both technological and economic disruptors, indications are that organisations are now ready to take the desktop estate forward again.
As business plans roll out, however, new factors are playing an important role. These include the consideration of risk-related matters such as data encryption on laptops, along with looking at the use of remote device lock or wipe mechanisms for lost or stolen systems.
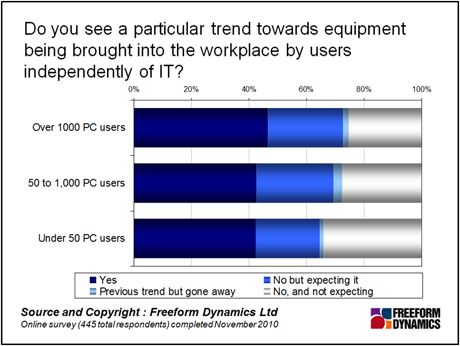
If this isn’t enough, into the mix is thrown the thorny issue of consumerisation, with users increasingly bringing their own devices into the workplace, whether IT supports them or not.
Recent research by us highlights that many organisations are considering refreshing their desktop estates or have already begun projects in this area. While it is clear the usual desktop refresh cycle has been interrupted by both technological and economic disruptors, indications are that organisations are now ready to take the desktop estate forward again.
As business plans roll out, however, new factors are playing an important role. These include the consideration of risk-related matters such as data encryption on laptops, along with looking at the use of remote device lock or wipe mechanisms for lost or stolen systems.
If this isn’t enough, into the mix is thrown the thorny issue of consumerisation, with users increasingly bringing their own devices into the workplace, whether IT supports them or not.
Overarching all this activity, considerable thought is then being placed on working out just what role, if any, desktop virtualisation will play in the refreshed estates.
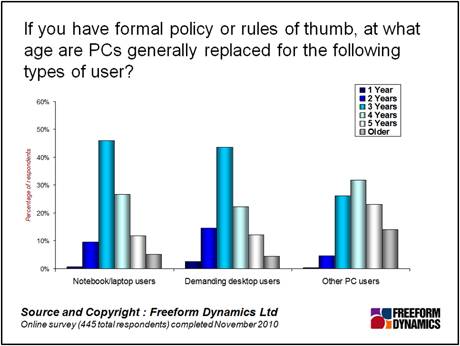
We have found that organisations have today settled on, or at least hope for, a three to five year life expectancy for their mainstream PC systems. Laptops and the machines of today’s more demanding users tend to be replaced more quickly, possibly being passed on to other users.
Having said this, quite a few organisations are sitting on some pretty old kit.
Most machines used in business today are still running Windows XP, which is now 10 year old technology. In the same study, we found that two-thirds of the respondents had XP deployed on at least half their current desktop estate.
With desktop estates generally aging due to economic pressure and reluctance to deploy Vista, a degree of pent-up demand now exists, with a focus on moving from XP to Windows 7. It is notable that Windows 7 has already overtaken Vista in mainstream business deployment.
We believe that 80 per cent of Windows-centric organisations have Windows 7 on the agenda in some form. These numbers are much higher than might be expected when you compare it with the desktop refresh activity of previous years.
So it will come as no surprise that desktop hardware refresh and OS upgrade activity are linked.
While these figures need to be treated with due consideration of the self-selecting nature of Web survey respondents, it is clear that desktop estates are about to change. Users’ desire to employ an expanding portfolio of devices, along with the above-mentioned consumerisation trend, is likely to create considerable support challenges.
This trend will be exacerbated by a need to secure corporate data effectively wherever it is stored or processed.
One area where organisations need considerable input from their channel partners concerns the implementation of total ‘solutions’ that are effective and manageable in daily operations where IT staff are under considerable stress.
Organisations are equally likely to ask for help simply backing up the data on user devices, an area still covered poorly in many businesses. Advice will also increasingly be sought on whether and how virtualisation is relevant, and partners are more likely to be asked for services in this area through 2011 and beyond.
In this context the beast that is security raises its head. With an expanding portfolio of devices to be supported, some perhaps not owned outright by the business, organisations will need complete solutions that protect systems.
These may include encrypting information on hard drives and also remote-wipe capabilities should devices be lost or stolen. The days of merely supplying desktop hardware and boxed software really are coming to an end.
CLICK HERE TO VIEW ORIGINAL PUBLISHED ON

Registration Required