By Tony Lock
The scope and sophistication of the IT security threats facing your organisation and the data you hold are expanding. Changing staff working patterns and the desire of users to utilise an increasing range of devices, not all of which may be owned by the organisation, are adding to the security challenge. A recent report by Freeform Dynamics illustrates the state of IT security today and provides some guidance for CIOs to understand the IT Security Jigsaw. A standout result highlighted by the research shows that the lack of security awareness as well as people making mistakes are seen to be greater challenges than malicious threats.
Most organisations are keen to improve the productivity of their workers and for many the use of IT solutions is expanding. At the same time, the expectations of users is that they should be able to access almost any information at any time of day and from almost any device, some of which may be personally owned rather than issued by the organisation.
The result is increasing numbers of users, internal staff along with suppliers and partners, accessing ever greater volumes of corporate information. Significant classes of the information may be either ‘commercially sensitive’ or subject to regulatory and governmental requirements requiring data protection and security.
The report shows the security challenges posed by the increasing use of IT systems, the changing expectations of users, evolving working practices and the growing sophistication of external security threats are well recognised inside a vast majority of organisations.
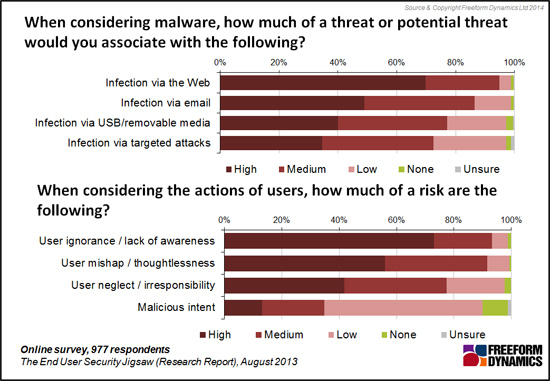
Figure 1
An important consideration raised by Figure 1 is that ‘human factors’ potentially pose just as great a challenge to IT security as do malware infections and targeted attacks. Indeed, the lack of security awareness amongst users, people making mistakes or simply not thinking about information security are rated as being bigger challenges than the threat posed by malicious intent form either inside the organisation or targeted attacks from outside.
This is an area where CIOs need to convince their peers of the importance of training users to understand not just what to do in terms of IT security, but why such processes and practices are important to the business.
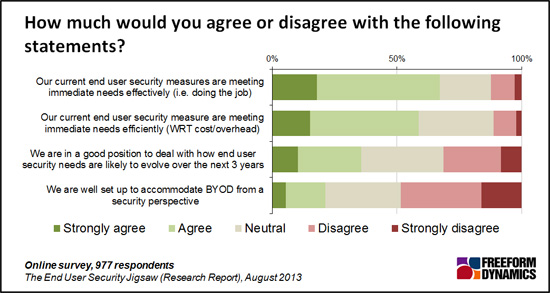
Figure 2
The research shows that already significant numbers recognise existing security measures are ineffective. (Figure 2) Even more importantly, when looking at the next three years, considerably under a half of think they are well placed to handle end user related security requirements as they evolve.
The survey revealed the proportion of organisations confident they can securely accommodate use of personally owned devices accessing corporate systems and data, often referred to as BYOD (Bring Your Own Device), is very low, and there is little evidence that this has altered materially over the intervening period. With threats increasing, legislative requirements growing and users demanding ever more flexibility and choice, this state of affairs is less than ideal.
The potential consequences of poor end user IT security can be extreme. With data protection laws placing stringent regulation on many types of data, from customer records to staff details, the impact of security breaches can now result in direct financial costs. The scale of fines for data breaches are going up. A quick scan of any internet search engine will show many examples of lost laptops resulting in fines and customer reparation costs.
But any security breach that impacts customer confidence in the brand of the organisation can be even more harmful. Should valuable intellectual property be compromised, long term effects can be even more damaging. Customers do not like to have their financial details compromised or sensitive records exposed.
With tablets and smartphones being even more easily lost or ‘left in the taxi’, the situation is likely to improve without steps being taken to improve user awareness as well as ramping up security deployed on portable devices.
Security for end users gives the CIO many elements to balance and assembling solutions can resemble piecing together a tricky jigsaw without a picture. The research identified six key pieces of the jigsaw that IT professionals in organisations confident in their capabilities put together to help improve end user IT security. (Figure 3)
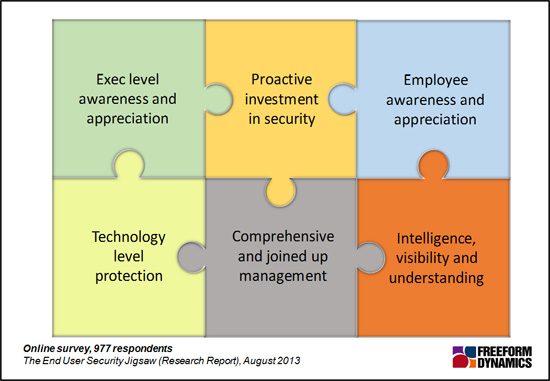
Figure 3
Some of the pieces identified will not surprise any CIO, although they can sometimes be difficult to explain to other board members to obtain budgets. The benefits of comprehensive and joined up management tools, both directly security related as well as solutions to administer the data and devices employed by users, are well understood.
However, with most organisations making use of a number of management tools already, many studies by Freeform Dynamics have shown it is often difficult to make a business case for further investment. Another jigsaw piece highlighted by those with greater confidence in their security capabilities is the value of having good threat intelligence available to inform awareness and shape responses to changing threats. Security confident organisations also recognise the importance of proactively investing in security management to ensure all the jigsaw pieces fit together smoothly to show the full picture.
Beyond technology, the remaining end user jigsaw pieces concern people related matters. These are usually the most difficult to address but putting them together is also likely to deliver the greatest benefits. Despite the high profile of ‘IT Security’ and the considerable publicity that security breaches bring, only one in five organisations not ranked as security confident have high levels of executive awareness of security issues. Even amongst those who are confident in security capabilities the number only just doubles. (Figure 4)
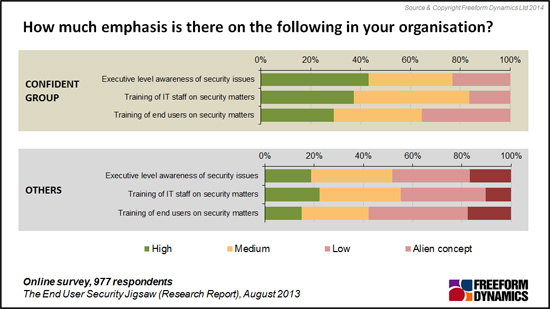
Figure 4
More importantly, the level of user training on security matters is inadequate with over half of organisations outside the security confident group stating such training to be an alien concept or low. Unless users, including ‘line of business executives’, understand IT security matters and why they are important the potential for accidental or targeted security breaches will remain high.
CIOs must seek to get security awareness and training high on the corporate agenda and budget planning if IT security is be enhanced, especially with user device proliferation expanding. Without this effective training in security and threat awareness, the best technology in the world is likely to still leave you exposed.
CLICK HERE TO VIEW ORIGINAL PUBLISHED ON
