In the last of this mini-poll series, we wanted to find out whether the security monitoring mechanisms you have in place are seen as effective. To kick off, we should introduce a couple of factors we thought might make a difference, namely whether you want to monitor, and whether you have to monitor against security breaches.
For the former we asked whether security monitoring was an investment priority – 45 per cent of the sample said it was.
For the latter we asked whether compliance was a driver for implementing monitoring capabilities – 53 per cent of the sample agreed.
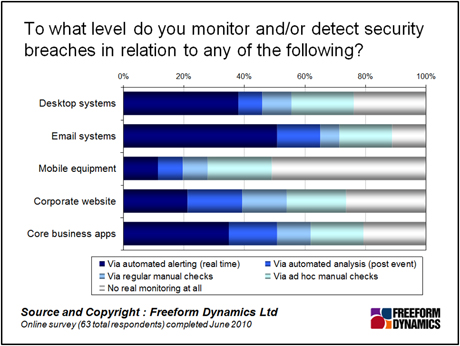
More on these sub groups in a minute – but first let’s look at what systems are currently being monitored. As you can see from Figure 1, the level of monitoring overall could loosely be described as ‘variable’ – email systems are the better of the class, whereas the emphasis on monitoring mobile equipment is relatively low.
So how does this picture change based on the “want to” / “have to” sub-groups? Taking compliance first, while it does make a difference, it’s not having a massive impact. Remember we’re asking about whether compliance is a major driver, so you might expect to see organisations a bit more, well, driven.
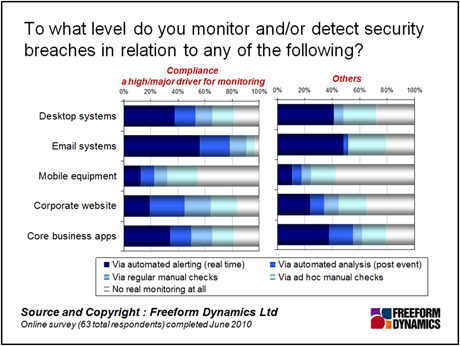
What you see here challenges the often-heard notion that compliance is an overriding driver for all risk-related investment. Clearly it is not. The reality is that reputational risk, operational risk, competitive exposure and the simple need for confidentiality in the normal course of doing business typically have a greater influence. It’s not just about ticking boxes to stay legal.
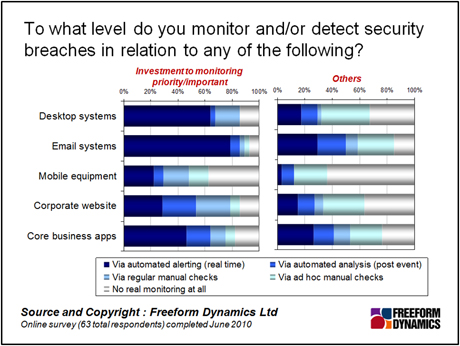
Whatever the drivers, it’s clear that money talks. Unsurprisingly, those seeing security monitoring as an investment priority have also made greater investments in such capabilities. In particular these are concerned with areas in which activity and risk are largely defined by the behaviour of end users. Email, desktop and mobile systems, for example, are all considerably better covered.
What’s specifically being monitored for? As you can see from Figure 4, dubious web site access is top of the list, followed by loss of corporate laptops and mobiles, and then data loss via email.
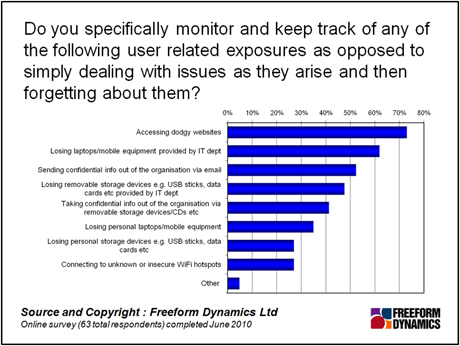
Perhaps what’s most interesting about this chart is how low down the list protections against personal equipment are. This is of course a tricky area – how can you lock down things that are outside your domain, most of which you have little visibility on? But equally we are seeing the amount of personal equipment in business use continue to rise. From a security perspective, this is an accident waiting to happen.
But what of the business case for investment? It’s all very well investing in improved monitoring facilities to help manage risk, but the benefit is difficult to get a handle on. Effective monitoring makes you more aware of the risks, so putting better systems in place can, ironically, actually elevate your perceived level of exposure. Meanwhile, those with poor monitoring facilities often see less in the way of threats, simply as a result of blissful ignorance. For these reasons, we didn’t see a huge difference in the reported level of challenges and risks in many areas when we compared those who had prioritized monitoring related investments to those who hadn’t.
But focusing on risk management anyway is a bit like trying to assess the return on investment from taking out insurance – you are better protected but it doesn’t really help with efficiency and effectiveness, ie the things that are front of mind in terms of day-to-day performance.
One area that did stand out, however, was the difference between groups when it comes to IT support overhead.
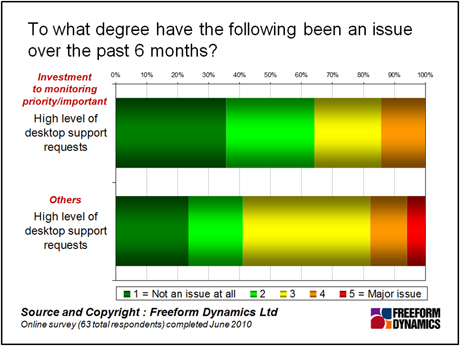
This is pretty important. It highlights the resource implications of security-related issues in general, in that someone, somewhere needs to spend time dealing with all incidents, large or small, when they arise. What we see on the above chart relates specifically to IT support overhead, but security related issues create extra work for business people too – investigating the impact of a security breach, dealing with public relations fallout, placating disgruntled customers, or simply filling out paperwork to document what’s happened. If we think of effective security monitoring as a way of pre-empting and preventing such issues arising, then it should be possible to work cost as well as risk into any business case.
So, if anyone still doubts that security can have a return on investment, just show them Figure 5 and see what they make of it.