Communications mechanisms in the workplace – from mobile devices to instant messaging and web conferencing – have proliferated over recent years. The days when a telephone was all you needed are long gone: nowadays, people juggle regularly between multiple mechanisms using various interfaces to communicate as they go about their jobs.
The resulting problem is that each mechanism has its own nuances that individuals have to tune into before it can work for them. So setting up a web conference, for example, may follow a quite different set of rules to setting up an audio conference. Moreover, these tools do not often interconnect seamlessly, even though there is an increasing need for them to do so.
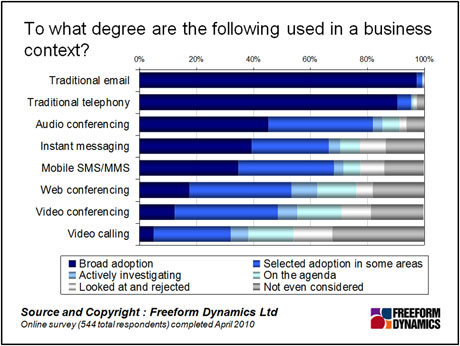
The chart, taken from recent research carried out by Freeform Dynamics into advanced business communications captures just how fragmented our work environments have become, with many businesses having a broad mix of communications mechanisms and tools. There are varying degrees of implementation of these tools across organisations. While some, such as traditional telephony and email, are widely used in the workplace, others, such as video-conferencing and mobile SMS, enjoy only partial adoption, or haven’t yet been implemented.
Contrary to what people on the receiving end might think, this fragmented environment isn’t a deliberate ploy by the IT department to make communications complicated. Rather, it has crept up on us over time, with newer technologies tending to find their own way into the workplace, instead of being implemented through a structured, integrated approach. This often goes hand-in-hand with poorly enforced rules around usage, which, in turn, tend to lead to things not being exploited properly. However, to fix this chain of events would be no easy task.
As a result, business users tend to muddle through with something that works for them, although not nearly as well as it could. Such a complex landscape makes communications highly inefficient. Resulting issues range from delays in getting necessary information from within the business, to poor intra-company collaboration and team coordination, and of course poor customer satisfaction. For example, the scenario where customer support wasn’t able to track down the right person to help deal with a query, and had to leave an irate customer with a promise to call back as soon as they managed to locate some assistance, will be familiar to many.
Beyond inconvenience, inefficiency and customer impact, however, lie more serious ramifications. Fragmented communications can lead to regulatory compliance blind spots, if information that needs to be captured falls through the cracks where different tools do not properly interconnect. Security breaches are much more likely as well, as a result of the numerous interfaces between the comms mechanisms being used. There is also the potential for incorrect or inappropriate advice to be passed around when “community” sources – either internally created by groups within the organisation, or, more worryingly, external sources such as Wikipedia – are exploited without any form of sanity check taking place.
This problem is not going to go away any time soon, and is one that businesses can’t afford to ignore. Of course, unified communications (UC) vendors will jump up and down and wave their arms with the offer of a fix-it-all solution. Fair enough: UC is designed precisely to deal with the ever-increasing communications fragmentation that companies are facing. But be warned. While implementing an overlay solution like UC in its various guises of unified messaging, unified directory, presence and so on, will help to deal with many of the issues mentioned, it is not a quick and easy fix. And unless it is done well, businesses are unlikely to be any better off.
Rather than get caught up in the hype of UC, companies need to have a good grasp of the issues they are facing, defined clearly in their own terms, and the impact on the business if the issues are not addressed. This should span not only what is happening at an infrastructural and application level, but also extend beyond it. Areas that should be addressed include how well processes are defined and executed, what policies are in place and to what extent they are enforced, as well as what role senior business managers should take to make sure things work.
The output of this exercise will likely be worth its weight in gold, as it will provide insight into where the biggest problems already lie, which helps companies to prioritise what needs to be dealt with straight away, whether this is with UC or not.
As always, we’re interested to know how this reflects your own situation, and how well you feel your own communications mechanisms hang together. Have you had any serious breaches as a result of a fragmented environment? And if so, have you a plan in place for dealing with these problems?