Patrolling an effective security regime is never a trivial task, despite the relentless development of security technology and services, because the information security management landscape is always challenging and always changing.
In days gone by, though, when the organisation owned and controlled all of the IT components, the information security challenge could at least be bounded, within the confines of the corporate infrastructure.
But nowadays we live in an increasingly ‘wired’ world where more and more people bring their own devices to work and, perhaps more significantly, their web services and social network accounts too. This means that the business world security defences will need to cope not only with all of the old challenges of mobile and remote working but also the new challenges of increasingly blurred boundaries between personal and working lives.
Net-savvy workers like to be always connected so they may look to use their own social media and instant messaging services, even when handling work-related matters. These are the people who might also use their personal web accounts either as workarounds, or to supplement business provided facilities.
For example, the ready availability of cheap, if not completely free, cloud-served data storage capacity can provide workers with quick and convenient data options. A few gigs here and a few gigs there can soon add up to a personal virtual datacentre, populated with a mixture of business-related data and purely personal information.
In the workplace most of these third-party services will be accessed and used via a web browser, usually requiring no client installation or configuration; which potentially puts them either completely beyond traditional IT management, or at least an arm’s length away.
What happens to business-related data once it has gone walkabout from the business environment is uncertain; data in the wild is almost never as well-managed or as secure as it would be if kept where it properly belongs and such feral data can pose a number of significant information management issues.
Our research shows that the two biggest concerns in relation to the use of personally acquired equipment and services for work purposes were: security and data loss (Figure 1).
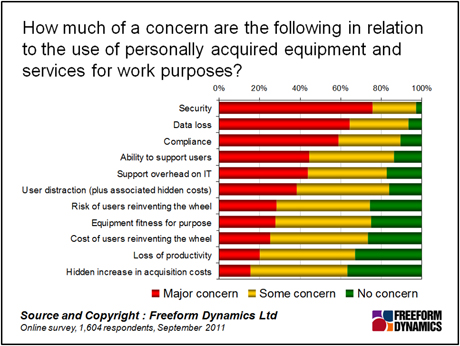
Figure 1
These headline concerns are not surprising and have been around ever since mobile and remote working first became established in our IT service portfolios. However, as the consumerisation of IT changes the landscape of the business IT infrastructure, the need for effective counter-measures becomes even more important.
Technology can help, but only as part of a blended approach that also involves user behaviour and business policy. The degree and sophistication of information security technology deployed will, of course, vary according to the needs and nature of the organisation, combined with the sensitivity of the data concerned.
Nevertheless, long-established but rudimentary measures, such as file transfer blocking and website/ port/protocol filtering, may need to be supplemented with newer and stronger measures – perhaps using tools for DLP (Data Loss Prevention) – which can improve mitigation of some of the risks associated with the potential loss of business data.
Managing user behaviour is not always so easy, though, because they may not be aware of the business risks involved in properly managing and protecting information and/or the rules and guidelines governing the use of privately-owned web services at work. Figure 2 shows that our research indicates that there is scope for the development, deployment and communication of effective end user policies:
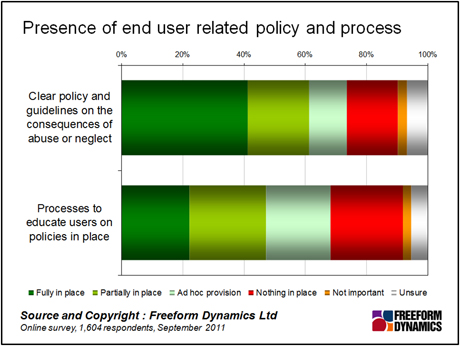
Figure 2
It seems that even where end user policies and guidelines for the use of personal equipment and services are in place, they are not widely underpinned by processes to educate users. This may mean that users are not only unaware of important security and compliance issues, such as data protection and privacy but also unaware of the undesirability of keeping, or using, business information in a private system.
Clearly, key consumerisation messages need to be better shared, understood and accepted, in the interests of mutual responsibilities, obligations and protection.
Incomplete or out of date information is never a sound basis for effective decision-making so it is vital that business information is kept together, in a business information system – not a privately-owned service that is unavailable to colleagues and stakeholders. The worst case is that the most up to date business information is not properly held and protected.
As ever, when it comes to protecting business information in a world of growing IT consumerisation, prevention is the best cure but this will require a strong combination of diligence, engagement, communication and co-operation between the employing organisation and the staff owners of personal web services and accounts.
CLICK HERE TO VIEW ORIGINAL PUBLISHED ON

Through our research and insights, we help bridge the gap between technology buyers and sellers.





Have You Read This?
From Barcode Scanning to Smart Data Capture
Beyond the Barcode: Smart Data Capture
The Evolving Role of Converged Infrastructure in Modern IT
Evaluating the Potential of Hyper-Converged Storage
Kubernetes as an enterprise multi-cloud enabler
A CX perspective on the Contact Centre
Automation of SAP Master Data Management
Tackling the software skills crunch