By Tony Lock
In a recent survey over 400 respondents gave us the inside track on the current state of corporate networks and their ability to handle changing work patterns. In particular, you make the case that your networks are ill prepared to tackle the increasing diversity and sophistication of security threats. As you see it, the days security based around the concept of a strongly defended perimeter are over.
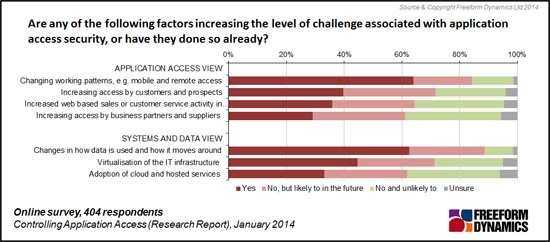
Figure 1 highlights that changes in the way your users, partners and customers access your systems is already causing security problems. In particular changes to way people work, along with their need to access enterprise data remotely or whilst mobile, are increasing security challenges, or are expected to do so in the near future.
Figure 1
As well as changes to how applications and data are accessed by users, modifications to the back end infrastructure are also posing security issues. Factors including alterations to how data is stored and moved around the IT infrastructure and the use of ‘virtualisation’ solutions, now well established in many organisations, are security concerns for a majority of respondents. The adoption of cloud and hosted services are also increasing security challenges for many of you.
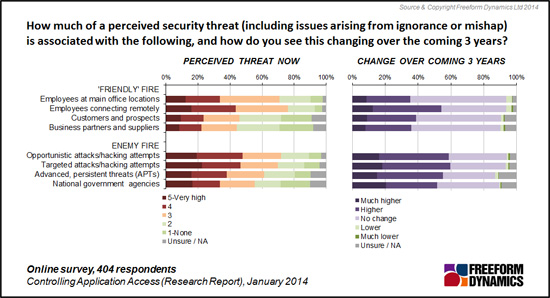
The survey also reveals where the security challenges are perceived to originate (Figure 2).
Figure 2
As the chart reveals, the scale of the threats from users working inside the enterprise or amongst business partners and suppliers are perceived to be almost as high as those originating from ‘outside the business’. Just as importantly, all are expected to escalate in severity going forwards
Of the internal threats, you clearly rank employees to be the biggest source of problems, through mishap, lack of knowledge or malicious intent. The security challenges associated with users connecting remotely is the single biggest issue, and is also the one expected to grow in severity going forwards.
When it comes to security threats from outside the enterprise, readers rank all vectors to be similarly challenging. Opportunistic attacks and hacking are perceived to be just as big an issue as more targeted attacks singling out the organisation. You see APTs to be almost as big a problem, a conclusion that can also be made of the security threat you see posed by the actions of ‘government agencies’.
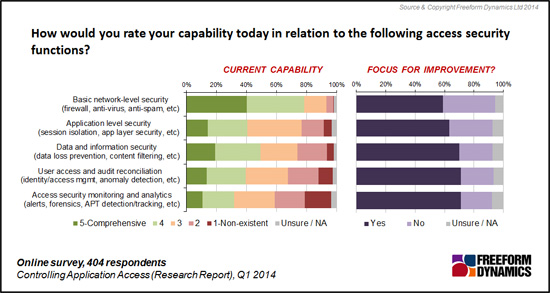
With so many areas seen to be challenges, and the nature of such threats becoming ever more complex, how well prepared are you to keep systems and data safe (Figure 3)?
Figure 3
Your responses make it obvious that with the exception of looking after basic network level security (firewalls, anti-malware etc.) the majority of respondents recognise a wide range of security management capability deficits. Recognition of the severity of threats faced and the management mismatch in capabilities to face them can be seen as the vast majority of readers highlight all areas as being foci of improvement.
While respondents recognise the need to improve all elements of network access and security, the survey posed a question asking if merely updating existing security solutions incrementally is good enough. The answer you give is a resolute ‘No’.
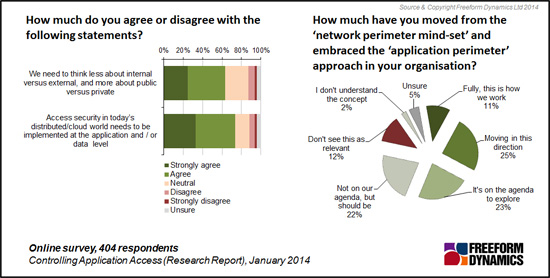
A clear majority of respondents agree that securing the perimeters of the enterprise is no longer a tenable approach. Instead the approach favoured is to attempt to secure individual borders around applications and data sets rather than the enterprise itself (Figure 4).
Figure 4
The issue you face is how to effect the transition to such a radically different approach to security from where you are now? The challenge is especially great as only a small number of your organisations have already made such a transition, making best practise hard to find. Modifying the security architectures in your organisations is complex as few of you are likely to be able to build a parallel infrastructure alongside your existing systems.
In practical terms this could mean you defining application-aware policies in the network that are applied irrespective of the physical location of the application and data. Such an approach has the benefit that if one application or data set is compromised, others are not automatically exposed as security is applied independently.
The adoption of application and data set security should also result in protection better able to mitigate against many internal threats. But architectural modifications to the technological security infrastructure will also necessitate you adopting new processes and procedures, in particular an application centric mind-set.

Tony is an IT operations guru. As an ex-IT manager with an insatiable thirst for knowledge, his extensive vendor briefing agenda makes him one of the most well informed analysts in the industry, particularly on the diversity of solutions and approaches available to tackle key operational requirements. If you are a vendor talking about a new offering, be very careful about describing it to Tony as ‘unique’, because if it isn’t, he’ll probably know.



Have You Read This?
Generative AI Checkpoint
From Barcode Scanning to Smart Data Capture
Beyond the Barcode: Smart Data Capture
The Evolving Role of Converged Infrastructure in Modern IT
Evaluating the Potential of Hyper-Converged Storage
Kubernetes as an enterprise multi-cloud enabler
A CX perspective on the Contact Centre
Automation of SAP Master Data Management