Ignoring key trends could be harmful to corporate health
Is it really true that organisations today are faced with a tidal wave of demands from ‘Generation Y’ employees to connect their personal devices to the corporate network? Certainly, if one goes by media headlines or vendor claims. Not at all, if one listens to those IT executives who flatly state that this sort of thing would never be tolerated in their organisations.
To get a better feel for what’s really going on, in September 2011 we carried out an online survey of 1,600 IT and business professionals. We asked about their own preferences and habits with regard to personal technology. We also investigated what’s going on within their organisations with regard to ‘bring your own device’ (BYOD) and the business use of consumer services such as instant messaging, web conferencing or online storage.
Our findings showed that the tidal wave is myth rather than reality, which in turn gives IT some breathing space. We also exposed three further key myths, which are:
• Generation Y is the driving force behind BYOD
• Consumerisation is all about the ‘hottest gadgets’
• It’s possible to stop consumerisation
So if it’s not Generation Y, who is it that’s pushing to have their own devices connected to the corporate network? As can be seen in Figure 1, outside of the IT department itself, it’s the senior executives who are most insistent on using a personal device for work.
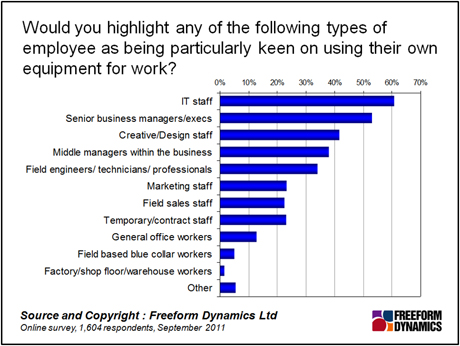
Figure 1
Furthermore, senior executives are the ones with the most clout, and the greatest likelihood to have their wishes granted. “Come back when the answer is ‘yes’” was the alleged response from a senior manager when told by IT that the security risks were too great to give him access to corporate applications on his new tablet device. This kind of incident could of course be used to engage the business in the necessary discussion on what’s needed to facilitate access in a secure and controlled manner. But all too often, the executives have their wish granted, while the underlying issue – access to corporate resources by privately owned devices, and all the risks associated with it – remains unsolved.
Let’s take a closer look now at what those devices are. Contrary to what the headlines might imply, and what is being reinforced by vocal executives waving around the latest tablet, mobile gadgets in the form of smart phones and slates are only part of the story. Windows-based desktop PCs as well as notebooks together account for a larger percentage of personally owned kit used extensively for work purposes than that running MacOS and iOS (Figure 2, responses rated ‘5’).
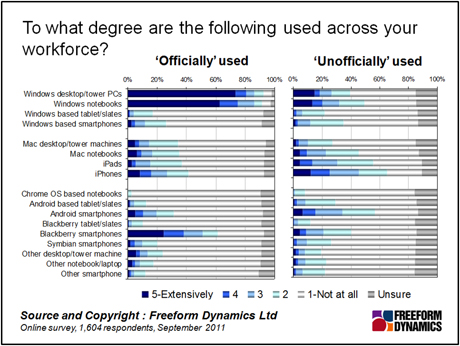
Figure 2
As time goes on, this balance may well change.
But the key issue remains the same: what policies and technology solutions are required to support safe and appropriate access to corporate systems using personally owned devices? IT departments need to make sure they don’t deploy point solutions that can support only a specific gadget type or two.
There is of course another approach to employees’ desire to connect personal equipment to the corporate network, and that is to ban it completely. Given the sensitive nature of the data held by many private and public sector organisations, as well as the potential consequences of such data falling into the wrong hands, such a restrictive approach is understandable. However, we believe it is not tenable: responses to our survey show that even in organisations where connecting a personal device to the corporate network is banned, it is happening anyway (Figure 3).
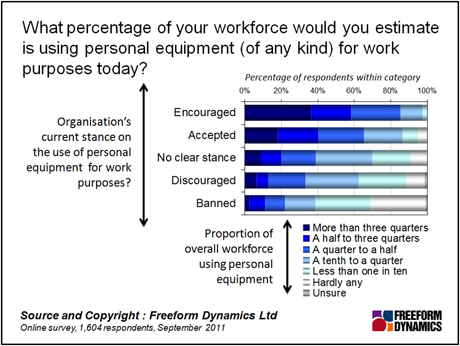
Figure 3
Fortunately, we’re not at the point where BYOD has become an unstoppable tide threatening to overwhelm IT departments. Equally, those who work on the assumption that they can either ban the use of personal devices for work purposes, or who feel that they can postpone taking action, are potentially putting their organisations at risk. Whether it’s because of pressure from senior management to access corporate resources from their personal tablet device, or employees resorting to consumer services (such as cloud-based storage), IT and the business will collectively have to face up to the reality that this is a trend that cannot be stopped in its tracks.
Having a consumerisation strategy in place is of critical importance. Such a strategy needs to focus on policy and technology in equal parts. From a technology monitoring and management perspective, it is important to ensure that the strategy is inclusive and covers as many device types as is realistically possible, not just the hottest gadgets. Equally important are business buy-in and support for any limitations that have to be put in place to safeguard the organisation’s security needs.
If you’re interested in more findings from our survey, you can download the full report for free here.
CLICK HERE TO VIEW ORIGINAL PUBLISHED ON

Content Contributors: Martha Bennett
Through our research and insights, we help bridge the gap between technology buyers and sellers.



Have You Read This?
Generative AI Checkpoint
From Barcode Scanning to Smart Data Capture
Beyond the Barcode: Smart Data Capture
The Evolving Role of Converged Infrastructure in Modern IT
Evaluating the Potential of Hyper-Converged Storage
Kubernetes as an enterprise multi-cloud enabler
A CX perspective on the Contact Centre
Automation of SAP Master Data Management