Mobile security is becoming more of a headache as the crossover between business and personal activity continues to increase, and employees generally expect more freedom. Research suggests, however, that you can only push technology-based protection so far before users rebel and try to find ways around it. To manage risks effectively, you therefore need to address the human factor.
Opposing pulls
Many IT professionals are of the opinion that the world would be a better place without mobile technology. Life was so much easier before users, particularly the more influential ones, discovered what they could do with smart phones and tablets.
One of the problems from an IT perspective is that modern mobile devices are both extremely powerful and extremely versatile. Users can connect them up to pretty much anything they want to very quickly and easily – unless, of course, you take steps to lock things down.
And there’s the rub. A big part of the appeal for users is the freedom, flexibility and convenience offered by mobile technology, so if the IT team constrains what they can do with their devices on risk and compliance grounds, much of that perceived value is undermined. Conversely, if users are allowed to run amok and some horrible data breach occurs, then IT will have to sort it all out. They may even get blamed for not having the necessary controls in place.
Who wins and to what extent varies between organisations, and even between IT and different groups of users. Senior managers and other users with political leverage usually get their own way; it’s hard to say no to the person who controls salary rises and bonus payments, or the sales team that puts food on the table. Everyone else is fair game for locking down – IT can get its own way here, despite the disharmony likely to result among the users concerned.
A hollow victory?
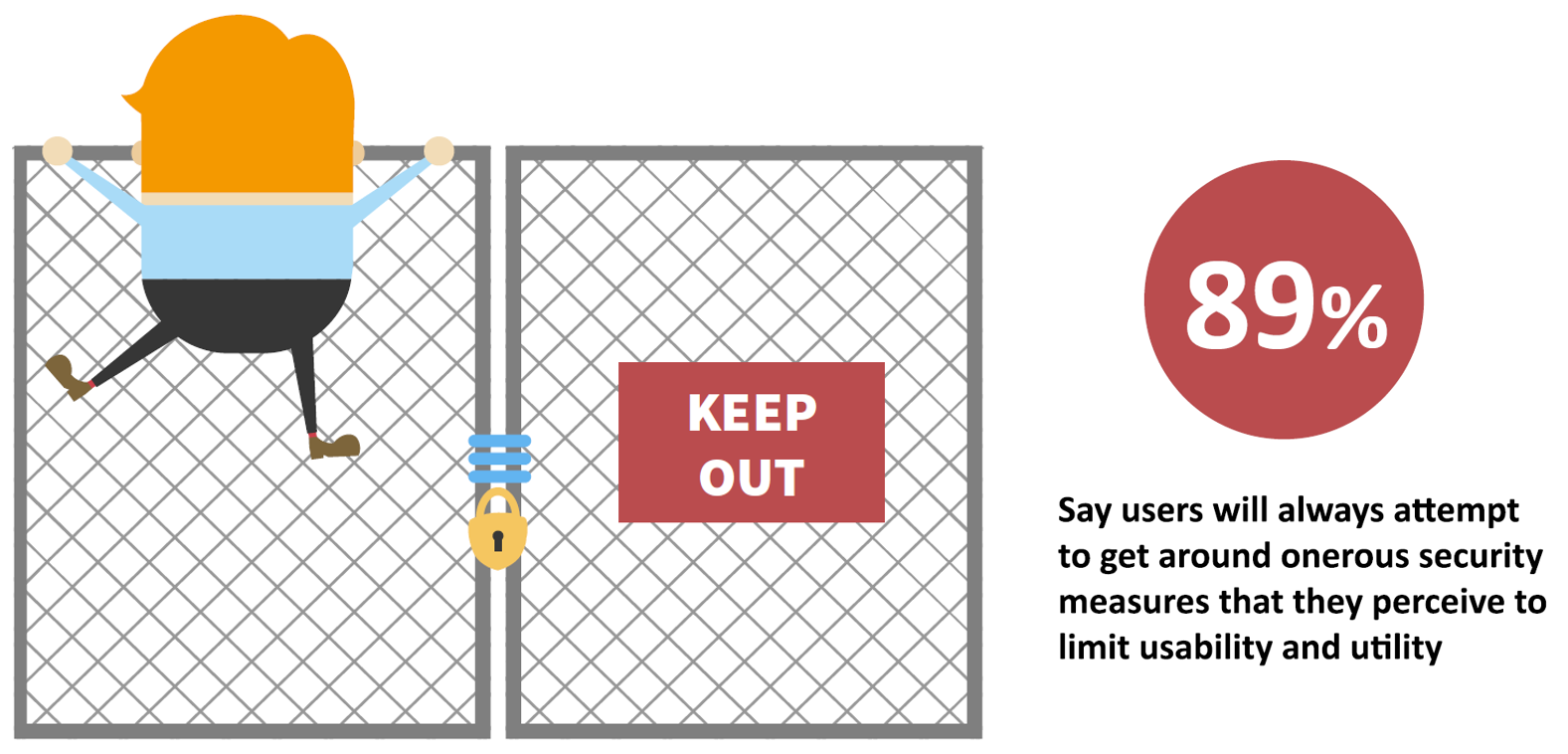
While IT teams often yearn for a standardised, locked down environment, recent research casts some doubt on whether being allowed to implement this, even for a subset of users, can be regarded as a solid victory for IT (Figure 1).
Click on chart to enlarge
Figure 1
The statistic we see here comes from a study in which just over 250 IT professionals provided feedback on various aspects of mobile security. It illustrates that users are not always as stupid as they sometimes seem. Try to get in the way of them doing what they want, and they can be pretty inventive about ways to get around the measures you have put into place.
Working with users, rather than against them
Against this background, findings from the same study suggest that the answer to this problem is not to get better at locking things down, but to adopt a different mind-set and approach. Alien though the concept might be to some IT professionals, the evidence tells us that working with users rather than purely against them can create a safer mobile working environment.
Sceptical? Well let’s walk through it.
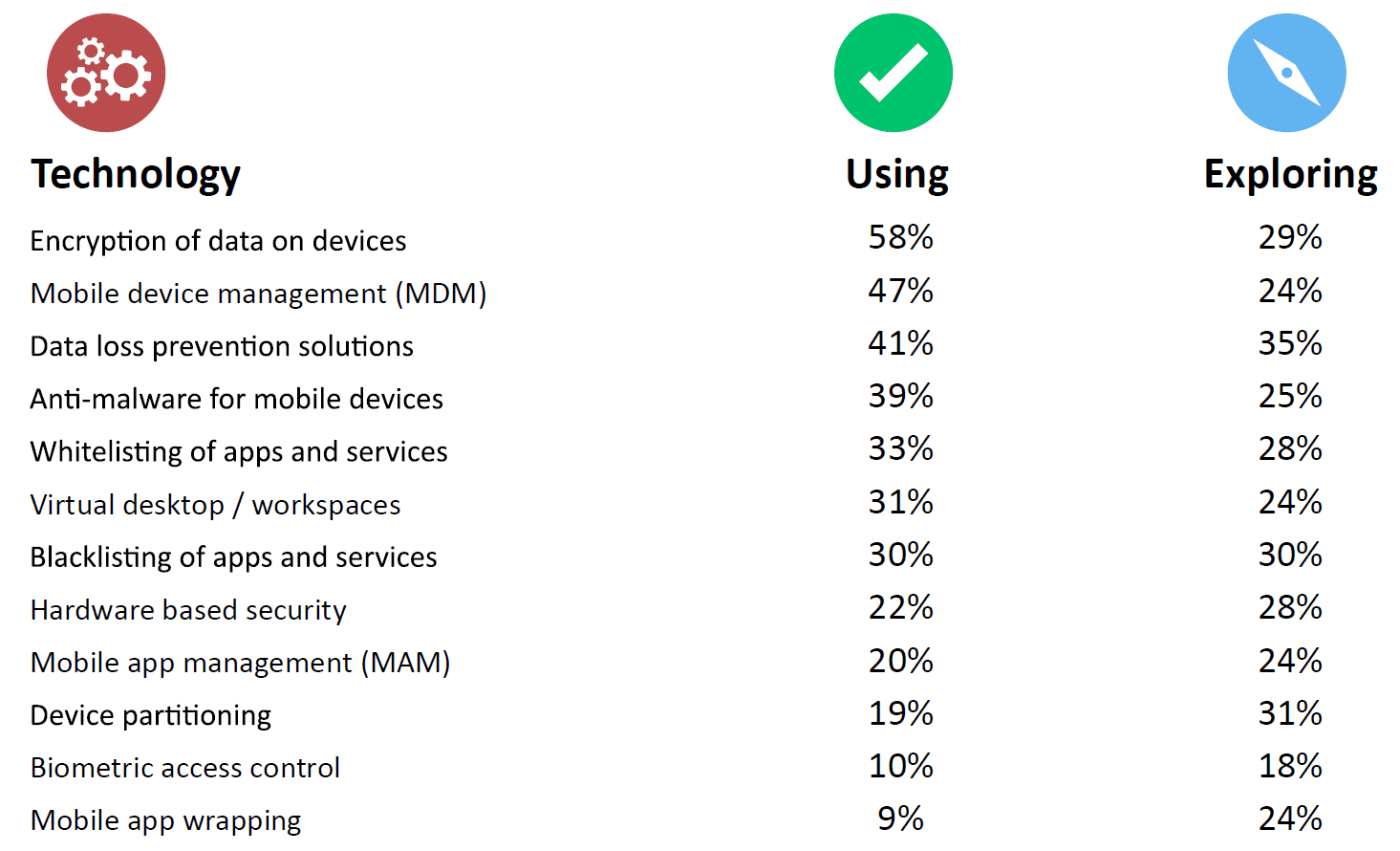
To begin with, many in the study reported they were using a range of technologies to help control the mobile security risk (Figure 2).
Click on chart to enlarge
Figure 2
Some had also taken steps to define usage policies and/or train and support employees to enable and encourage safer behaviour (Figure 3).
Click on chart to enlarge
Figure 3
Now for the sake of disclosure, we should point out that the numbers we see here in relation to both technology adoption and the presence of policies and training are likely to be inflated. Those with more of an interest in a topic are more inclined to fill out surveys on it. But that doesn’t matter in the context of our discussion here – we can still legitimately look at how approaches correlate with outcomes.
During our analysis, we used the technology adoption data to identify the subset of respondents investing significantly in physical control and lock down. We ignored the presence of policies because we couldn’t be sure of the form these took. Ringbinders gathering dust on shelves or documents buried deep in your intranet don’t really get you anywhere. We therefore homed in on training and support.
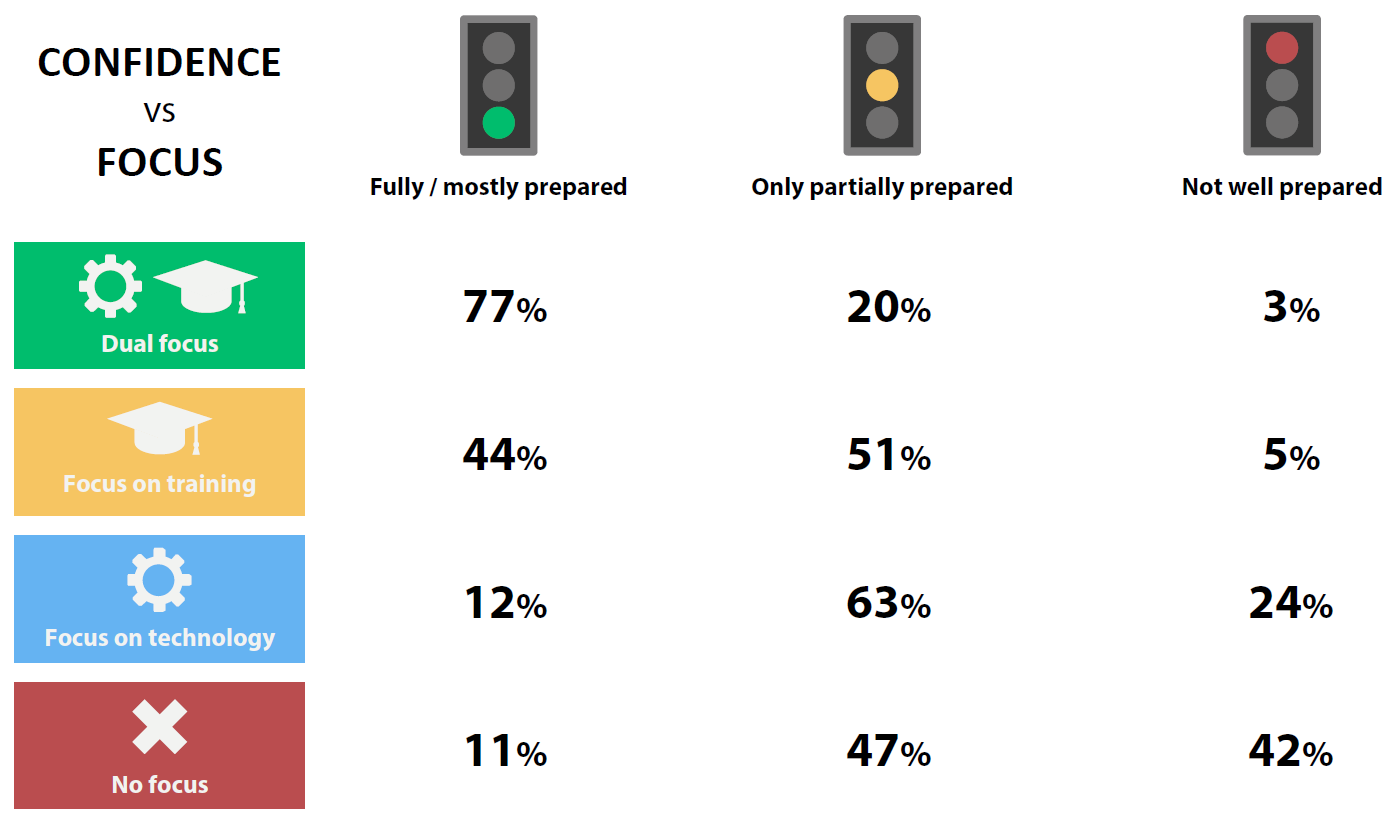
When we netted it out, we ended up with four groups – those focused on technology, respondents emphasising training/support, those combining the two into a dual focused approach, and others doing little or nothing. We were then able to look at how well respondents in each group felt they were prepared to deal with evolving mobile security challenges. The picture that emerged was pretty striking (Figure 4).
Click on chart to enlarge
Figure 4
Not surprisingly, most (77%) of those with a dual focus felt they were in a good position. What’s more interesting is that the group focused mostly on training and support on average felt significantly more confident than those relying mostly on control and lock down (44% vs 12%). In fact, comparing the bottom two rows, it would seem that simply throwing technology at the problem doesn’t get you very far at all.
The bottom line
The reality is that most security risks associated with mobile technology stem from user ignorance. Non-technical staff just don’t see the dangers as IT professionals do. Rather than write them off as being stupid or irresponsible, it therefore makes more sense to provide users with some straightforward pointers on how to be safe. Simple written guidelines coupled with short, sharp training delivered in context works well.
Technology-based measures still have their place, but don’t just focus on lock down and control. Monitoring tools can help you spot undesirable behaviour and step in as appropriate. Equally valuable are enterprise versions of popular file sharing services and app stores, or better still, digital hubs that provide users with a safe one stop shop for key documents and software. One way to break bad habits is to give people something even more convenient than the service you are trying to wean them off.
All of the above is a long way of saying that there is no single answer to the mobile security challenge. It’s about blending different measures in the right combination.
If you are interested in reading more about the research discussed in this article please download the study report entitled ‘User-Centric Mobile Security’. You can get your copy here.

Dale is a co-founder of Freeform Dynamics, and today runs the company. As part of this, he oversees the organisation’s industry coverage and research agenda, which tracks technology trends and developments, along with IT-related buying behaviour among mainstream enterprises, SMBs and public sector organisations.




Have You Read This?
Generative AI Checkpoint
From Barcode Scanning to Smart Data Capture
Beyond the Barcode: Smart Data Capture
The Evolving Role of Converged Infrastructure in Modern IT
Evaluating the Potential of Hyper-Converged Storage
Kubernetes as an enterprise multi-cloud enabler
A CX perspective on the Contact Centre
Automation of SAP Master Data Management