In a nutshell
Device proliferation and loss of control over at least some end user equipment drives a need to centralise key aspects of IT delivery in order to maintain service levels and manage potential costs and risks. But most IT teams are not fully prepared to deal with the new demands, meaning funding and resources may be needed to strengthen the end user computing environment. Fortunately, a range of business drivers are emerging to help build the necessary business case.
The end user computing game isn’t what it used to be
Gone are the days when end user computing was defined by the Windows PC. The results of a recent research study confirm that we are now living in a multi-platform, multi-device world in which user influence is growing rapidly:
- Over 90% see demand for the use of smartphones and tablets
- Over 50% see a trend towards Windows PC alternatives such as the Apple Mac
- Over 85% see demand for the use of multiple devices by individual users
- Almost 40% say that user preferences already significantly influence technology decisions, with over 50% seeing this kind of influence growing
- Over 80% report technology decisions being made independently of the IT team
Against this background, a key question is how best to deliver a good service to users while at the same time managing potentially escalating costs and risks.
IT teams know what’s needed, but most are not ready
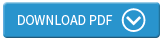
With the proliferation of devices and the loss of at least a certain amount of direct control over end-points, a good tactic is to centralise as much as you can (Figure 1).
Figure 1
The priority is to centralise data, and preferably execution too. Where this isn’t possible, then centralised management is the fall back position.
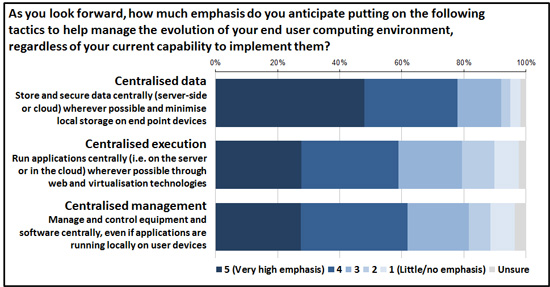
Of course these simple principles translate to a need for the right infrastructure to be in place either within your network or in the cloud. We won’t go into detail here, but you can imagine that solutions range from data and security management software, through access technologies and middleware, to various forms of virtualisation. The nature and mix of technologies will depend on your requirements, but whatever these are, the chances are that you have significant gaps in your armoury (Figure 2).
Figure 2
Note that the responses to this question are self-calibrating, i.e. the reference point used by participants in the research is their own assessment of needs, not some theoretical notion of perfection. The gaps referred to probably therefore reflect reality and a genuine need to invest.
Investment cases need to focus on the positives, and highlight key business benefits
When considering the rationale for investing in an infrastructure capable of handling an increased level of user control and flexibility, most IT professionals immediately focus on the risk management dimension. While perfectly valid, many in the research pointed out that business execs are often the most difficult to get through to when it comes to the importance of putting appropriate security and compliance measures in place. Indeed, the irony is that senior managers are sometimes the worst culprits in terms of flouting the policies and mechanisms implemented to protect the business, as these comments gathered in the research illustrate around the topic of ‘Bring Your Own Device’ (BYOD):
“Upper management has OK’d BYOD, ignoring input and warnings from IT, but users are mostly clueless about their real needs. Some devices will just not work in our environment, then people get angry when we can’t fix it.”
“End users and business management have lost any understanding of security and responsibility in the rush to be seen as fashionable.”
With this in mind, it generally makes more sense to build a business case for enhanced infrastructure and tools around more positive factors. An example at a detailed level might be the benefits of enabling users to do more with their desired equipment, rather than being constrained by compatibility issues and other limitations associated with the use of alternative or personal devices.
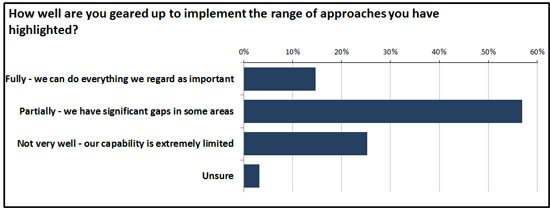
At a higher level, you can extrapolate and refer to benefits that users and business management often put forward themselves when trying to justify better access and a great degree of freedom and flexibility (Figure 3).
Figure 3
In some respects, BYOD activity and requests for broader device support can almost be regarded as a proof-of-concept exercise that users themselves have already performed. Either way, experience says that a positive case is more likely to resonate with senior decision makers than a negative one.
Want to know more?
In this Inside Track, we just touched on some of the challenges and opportunities associated with the evolution of end user computing. There’s clearly a lot more to this important conversation. For a more detailed presentation of our study findings and a discussion of the issues arising, we would therefore encourage you to download the full research report entitled “The Politics and Practicalities of End User Computing”, which is available here.

Tony is an IT operations guru. As an ex-IT manager with an insatiable thirst for knowledge, his extensive vendor briefing agenda makes him one of the most well informed analysts in the industry, particularly on the diversity of solutions and approaches available to tackle key operational requirements. If you are a vendor talking about a new offering, be very careful about describing it to Tony as ‘unique’, because if it isn’t, he’ll probably know.





Have You Read This?
From Barcode Scanning to Smart Data Capture
Beyond the Barcode: Smart Data Capture
The Evolving Role of Converged Infrastructure in Modern IT
Evaluating the Potential of Hyper-Converged Storage
Kubernetes as an enterprise multi-cloud enabler
A CX perspective on the Contact Centre
Automation of SAP Master Data Management
Tackling the software skills crunch