Professional IT prefers disciplined approaches which back up, or copy, all enterprise data to ensure it does not go missing. There are good reasons for this especially with core data (from transaction applications) when you bear business continuity and regulatory requirements in mind. When, however, you consider mobile devices (specifically mobile phones, tablets and even many laptops), the data loss prevention implications are not necessarily so clear or so obvious. Data loss prevention may already have been done for you, whether you are an IT Pro or an end user.
First, consider risk. A recent Freeform Dynamics Research Report — the “End User Security Jigsaw”, Figure 5 — shows the following:
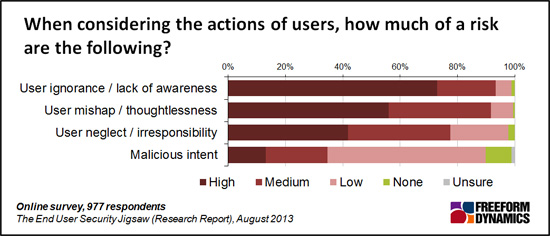
What is clear here is that it is user ignorance or lack of awareness, followed by mishaps and thoughtlessness, are what matters most. This seems to argue that IT should take responsibility for backing up and/or copying data on mobile devices — in order to prevent data loss.
Pause, however. Think what is on each typical smartphone and tablet and even some laptops (especially executive ones). Consider how these devices are used. Look at your own devices and think (just as Dale Vile, Freeform Dynamics’ CEO, asked me shortly after joining the firm).
Most mobile devices have an OS (whether iOS or Android or Windows or some other). They have apps or applications, the majority downloaded from the iTunes Store or Google Play etc., though some may come from internal enterprise app stores. There may be music, videos, books or magazines, social networking information, contact lists, sport data (like from the gym or from running outside), notes and more.
Now let us work through all of these and consider the implications in the context of data loss prevention.
Whichever OS you have on a device, there will almost always be a copy available on the Internet or from your vendor. This applies to iOS, Android and Windows. Yes, settings may be lost but, on most mobile devices, these are readily recreated if there is no copy in iCloud or in Google Mail, etc.
Similarly with apps and applications. If these are free, then they can be downloaded again from the original source at no cost. If they were bought, then the iTunes Store or Google Play, when you sign in again, will permit you to download these again. There is little risk of loss here.
For purchased books and videos and music, for example from Amazon or Barnes & Noble or Waterstones, the same is also true. You have reset your device accidentally but your data is recoverable from these existing stores.
For other music and videos the likelihood is that you will have used iTimes or Kies or simply a USB connection to transfer that data to your mobile device. This means you almost certainly have an alternative copy on a different machine (most probably a PC of some form). Or you might also choose to save this content into iCloud or some other cloud like Dropbox or SkyDrive.
Social networking is almost always performed with a connection to Facebook or to Twitter or to LinkedIn. In effect these are like browser sessions, where the data is not on the mobile device but in a remote server. Most ‘sport apps’ want you to interact, which means that you are uploading your (say) gym session data to a remote site. Ergo, there can only be minimal data loss here – because your app uploads for you. Indeed, most enterprise apps will be similar, because most enterprises do not want their data stored on mobile devices: they design their apps to ensure that most data is kept on their servers or is only accessible by authenticated browser sessions to enterprise hosted servers.
Photos, however, may represent a special form of data, because they are often (though not necessarily) created on the mobile device. This is content originated on the device, just like a note to yourself or a document against which you have made comments. The answer here is simple. You might manually save all newly originated content into an area that automatically syncs to a remote site (with a Dropbox or SkyDrive); or you can use tools like Evernote which will automate the saving of the original data off of the mobile device.
That leaves contacts, probably the most valuable and personal of all data on a smart device. Apple and Google and Microsoft all help here, as do the contact-copying services provided by various mobile telcos.
There is, nevertheless, one major exception – which predominately applies to mobile laptops (rather than smartphones or tablets). This is where a device is significantly used to originate content (of any form – writings, presentations, voice, videos, diagrams, music or whatever). Where this occurs IT may have to step in to prevent enterprise data loss, if the user will not take responsibility.
From the above it should be evident that nearly all data on most mobile devices has a copy existing already, or a user can simply and for free ensure that data copies exist. Ergo, for data loss prevention the risks are small, IT need not, therefore, worry about data loss prevention (other, perhaps, than to alert employees what is available and how to exploit capabilities they already possess). This is not, however, the same as mobile device security-enabling or usage policy settings or ensuring that any data created or stored on a mobile device cannot be read if (say) the device is stolen.
CLICK HERE TO VIEW ORIGINAL PUBLISHED ON

Content Contributors: Charles Brett
Through our research and insights, we help bridge the gap between technology buyers and sellers.



Have You Read This?
Generative AI Checkpoint
From Barcode Scanning to Smart Data Capture
Beyond the Barcode: Smart Data Capture
The Evolving Role of Converged Infrastructure in Modern IT
Evaluating the Potential of Hyper-Converged Storage
Kubernetes as an enterprise multi-cloud enabler
A CX perspective on the Contact Centre
Automation of SAP Master Data Management