Managing risk in business has always been more of an art form than a science. The same is true of the practice of managing IT risk. As we know, businesses today function effectively only when the organisation itself enjoys close working relationships with a diverse array of customers, partners, suppliers and other third parties. Such is the nature of routine operations that there is no effective alternative to having complex interactions with people and their supporting IT systems that spread far beyond the organisation’s IT firewall and, indeed, the business itself. Clearly this nature of working has profound implications for those charged with securing the operations of the business and the IT systems without which daily life becomes untenable.
It is also undeniable that the pressures inherent in modern business, especially the demand to respond rapidly to quickly fluctuating market conditions and customer expectations along with the need to work closely with third parties, are stressing IT security. However, there is another issue that is placing further tension on securing systems. This pressure has always been a factor but is now a very visible, not to say vocal, issue and it can be summed up as the “expectations of people”.
Working people are today far more mobile than ever before and unlike in the distant past, say two or three years ago, they now expect to be able to access all IT services on which they depend from almost any location, be it the home office, hotel bedroom, airport lounge, train bus and coffee shop at any time of the day or night. With the rapid growth of “commercially focussed” security threats there is a requirement that IT be able to actively manage the risk associated with all devices and information utilised by users, especially those who are mobile or who are working from outside of the enterprise firewalls.
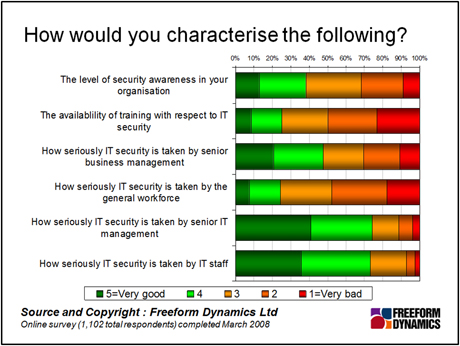
The need to manage the security of devices coupled with the inherent expectation that people have that the device “belongs to them” creates challenges. This becomes very apparent when one looks at the results outlined in the figure above. Even amongst IT staff “security” is by no means taken “seriously” by everyone, whilst when we look at the general workforce it is evident that both security awareness and overall attitudes leave a lot to be desired. Perhaps most worryingly of all it is evident that the availability of IT security related training, usually regarded as the most effective means of raising security, is not readily available in four organisations out of five.
So just how can the balance between “locking down” and “opening up” be safely achieved whilst ensuring that not only are IT and business risks managed, but that such risks can be monitored and routinely reported back to line of business managers and compliance officers? The first step is to ensure that the organisation has a policy in place that states, very clearly, that all IT equipment will be managed by the IT department (or whosoever is providing the device management service). It should also explain why and exactly how the management of the devices will be achieved along with stating the responsibilities of the user of the device in the process. It must also scope precisely what, if any, “freedom” the user shall have to personalise the device and how this can be achieved without negatively impacting security.
For routine security to be most effective our research
has shown that explicitly training the users of systems, especially those making use of mobile devices, how to operate securely is the single most effective measure that can be taken. Clearly machines need to be patched in line with the software providers’ directions and all necessary security tools should be installed and kept up to date. But it is essential that behaviour patterns be taught that reduce the potential for the machines to become compromised or for data to be lost or stolen. “Communication” is the key.
In the longer term it is likely that new solutions, especially in the realm of virtual desktop systems and holding all data centrally or the routine encryption of locally held information will enhance security whilst adding more scope for individuality to be displayed. But until everyone treats security with the respect required there will be a need for ongoing education of every business user of IT systems to raise awareness of security concerns and how easily security can be compromised, either by accident or design. It is worthwhile remembering the saying “Nothing is fool proof as fools are so ingenious”; whoever first said this must have had the users of IT equipment in mind. If they didn’t it shows a degree of foresight that borders on the clairvoyant.
Tony is an IT operations guru. As an ex-IT manager with an insatiable thirst for knowledge, his extensive vendor briefing agenda makes him one of the most well informed analysts in the industry, particularly on the diversity of solutions and approaches available to tackle key operational requirements. If you are a vendor talking about a new offering, be very careful about describing it to Tony as ‘unique’, because if it isn’t, he’ll probably know.





Have You Read This?
From Barcode Scanning to Smart Data Capture
Beyond the Barcode: Smart Data Capture
The Evolving Role of Converged Infrastructure in Modern IT
Evaluating the Potential of Hyper-Converged Storage
Kubernetes as an enterprise multi-cloud enabler
A CX perspective on the Contact Centre
Automation of SAP Master Data Management
Tackling the software skills crunch